Choosing between Microsoft SharePoint and OneDrive can fundamentally shape how you safeguard data, streamline workflows, and empower teams to collabor…
Jason Harlam
How to Create SharePoint Custom Permissions
Microsoft’s defaults are highly secure. In most cases, you will be able to find the right permission levels without customization. However, Microsoft also understands that there are edge cases and will account for them if you know where to look.
Follow These 9 Best Practices to Keep Microsoft SharePoint Secure
Microsoft SharePoint is one of the most popular collaboration tools in business. There is a good reason for this. Microsoft provides highly secure updates, and most devices are compatible with SharePoint. However, no matter how secure Microsoft is, it’s still...
Benefits of SharePoint for Businesses: Rethinking Digital Workflows
Businesses are under pressure to streamline collaboration and secure their data. Yet, according to McKinsey (2023), interaction workers spend about 28% of their week buried in emails or searching for information, time that could be spent driving results. When...
How to Perform a Microsoft Teams and SharePoint Integration
Every day, the average worker toggles between different windows or applications 1,200 times. As a result, the average worker loses 4 hours of productivity per week to switching tabs. The best way to reduce that lost time is to unify your work applications as...
What is Cloud Disaster Recovery and How It Works with Onsite Systems
Downtime doesn’t just stall operations; it damages reputation, erodes customer trust, and drains revenue. According to the Uptime Institute, over two-thirds of IT outages now cost more than $100,000, making resilience a business-critical priority. Yet many mid-sized...
Cloud Database Advantages That Give Businesses an Edge
Growing businesses can’t afford downtime, complex infrastructure, or rigid systems. Traditional databases often come with high upfront costs, maintenance challenges, and limited flexibility. According to Statista, over 60% of corporate data is now stored in...
The Ultimate Cybersecurity Assessment Checklist for Better Protection
The line between safety and exposure is just one missed security update away. According to IBM’s 2024 Cost of a Data Breach Report, the average data breach now costs organizations a staggering $4.88 million—a sharp reminder that cybersecurity is no longer just an IT...
7 Encryption Benefits That Safeguard Growing Businesses
Small and mid-sized businesses (SMBs) are in the crosshairs of cybercriminals like never before. What used to be a problem for global giants is now a daily risk for companies with modest IT budgets and limited cybersecurity resources. Yet many SMBs still...
8 Cloud Malware Risks to Be Aware of So You Can Prevent Them
In many ways, using a cloud infrastructure is more secure than hosting your data on-premise. 94% of businesses notice improved security after moving to the cloud, and 91% say it helps them meet their compliance requirements more easily. However, cloud malware...
Why IT Process Automation is Your SMB’s Secret Weapon
Running a small or mid-sized business (SMB) comes with its fair share of challenges—limited resources, growing operational demands, and the constant need to stay competitive. But what if there was a way to streamline workflows, reduce errors, and free up your...
7 Game-Changing Benefits of Microsoft 365 for Business
You’ve probably heard about cloud-based solutions, but if you’re like many small and mid-sized business leaders, you’re searching for something that delivers real results without overwhelming your team. The good news? There’s a suite of tools that’s designed to...
Don’t Let Hackers Deface Your Data: What is Cyber Vandalism?
According to Allianz Risk Barometer, 45% of experts consider cyber incidents to be the most dreaded cause of business losses, surpassing both natural disasters and energy concerns.“We are in a time where data is currency, a single act of vandalism can bring any...
Why Cybersecurity Is Important for Sustaining Business Growth
It’s well known that any business (or individual) that stores anyone’s personal information (including their own) needs a solid cybersecurity strategy to protect themselves and others from identity theft. Failing to do so can cause irreversible reputational...
Essential SMB Cybersecurity Tips For Business Owners on The Go
Small and medium-sized businesses (SMBs) are big targets for cyber attacks. By the end of 2024, 1 in 3 SMBs faced cyber threats of varying severity. The reason why hackers target smaller organizations is because they assume that SMB cybersecurity measures are...
What to Look For in Managed IT Services [Checklist]
Choosing a managed services provider (MSP) can be a long, time-consuming process. Understandably, you want to carefully select the best provider for your needs. However, this can’t come at the expense of countless business hours. Using a comprehensive managed...
Cloud Security Assessments: What They Are and Why You Need Them
As more businesses move to the cloud, cloud security assessments have become essential for safeguarding sensitive data. However, many companies fail to assess their cloud infrastructure regularly, leaving critical security gaps. In fact, 80% of companies have...
How to Handle Support Tickets for Efficiently IT Management
IT issues are inevitable in any business environment. From simple password resets to critical system outages, managing support tickets efficiently is crucial for maintaining smooth operations. The average employee spends about 22 minutes a week dealing with IT...
MFA vs 2FA: Understanding the Best Security Approach
Introduction to MFA vs 2FA Cyberattacks are increasing, and weak authentication remains a top vulnerability. 81% of breaches are due to stolen or weak passwords. This highlights a critical problem for businesses relying solely on traditional login methods....
Cloud Migration Steps: A Complete Guide to a Smooth Transition
Cloud adoption impacts more than just IT departments. By moving your infrastructure to a cloud platform, you can adopt agile methodologies, update processes quickly, and respond rapidly to market changes. However, to take advantage of these benefits, you...
What Is the Difference Between IT Support Tiers?
The difference between IT support tiers is based on the complexity of the issues handled. Lower tiers handle simple tasks like password resets, while higher tiers handle more complicated problems. As a result, different support levels also require technicians...
What’s The Difference Between Staff Augmentation vs. Managed Services?
The difference between staff augmentation vs. managed services is that staff augmentation involves hiring external personnel temporarily to fill specific roles, while managed services involve outsourcing entire IT functions to a third-party provider....
Why Cloud Computing is Important for Business Success
In a rapidly evolving business environment, organizations face the constant pressure to stay competitive while managing costs and improving efficiency. Traditional IT infrastructures often struggle to meet these demands, leading to operational bottlenecks and...
Cloud Security Threats: How to Identify and Defend Against Them
With the increasing adoption of cloud services, businesses face an escalating threat landscape. In 2023 alone, data breaches exposed over 26 billion records globally, with a significant portion tied to vulnerabilities in cloud environments. Jason Harlam,...
What is Data Breach Insurance & How Do You Know When You Need It?
The impact of data breaches on SMBs can be catastrophic. According to statistics, 60% of small companies close within 6 months of being hacked. Much of the reason for this stark number comes from the fact that these companies cannot afford the costs associated...
A Step-by-Step Guide to Creating a Network Security Plan
Data breaches and cyber-attacks are more common than ever. Many businesses underestimate the importance of a robust network security plan until it's too late. As Jason Harlam, Business Development Manager at Technology Advisory Group, says, “Implementing a...
IT Infrastructure Outsourcing: A Comprehensive Guide for Businesses
Businesses today face challenges in managing their IT infrastructure efficiently. Maintaining in-house IT teams and systems can drain resources and distract from core business activities. Companies often struggle with high costs, inadequate expertise, and the...
Effective Cloud Migration Strategies for Modern Businesses
The decision to migrate to a cloud environment can often come from the need to reduce costs and improve efficiency, but without a solid cloud migration strategy, companies face significant risks of increased downtime and spiraling costs. I In fact, research...
How to Protect Your Business from Cyber Threats on National Work From Home Day
Working from home offers unparalleled flexibility, allowing employees to achieve a better work-life balance and avoid the daily commute. However, this shift also brings increased cybersecurity challenges. With more people accessing company networks from home,...
Why Managed IT Services Are Better for Your Business Growth
Navigating the complexities of IT management without a robust support system can leave businesses struggling with inefficiencies and missed opportunities. As Jason Harlam, Business Development Manager at Technology Advisory Group says, “In a scenario where...
Navigating Through BYOD Security Risks
The pandemic and its aftermath ushered in an era of remote work, leading to a significant increase in the adoption of Bring Your Own Device (BYOD) policies. 47% of respondents reported an increase in BYOD during the pandemic. This shift allowed employees the...
Backup Basics: A Detailed Guide for World Backup Day
In this day and age, where data is as precious as currency, the peril of losing essential information is a pressing concern. The sting of losing a day's work—or worse, years of accumulated memories and data—is a harsh reality many have faced in the digital age....
What Managed Services Mean for Today’s Business Landscape
Navigating the complexities of information technology is increasingly challenging for today’s businesses. A startling statistic reveals that 82% of companies have encountered at least one unplanned downtime event in the past three years, underscoring the...
Navigating Technology Issues in Business: A Comprehensive Guide
In an age where technology underpins every aspect of business, IT problems have become a common yet critical concern for companies of all sizes. These problems are more than just minor inconveniences; they represent significant hurdles to efficiency, security,...
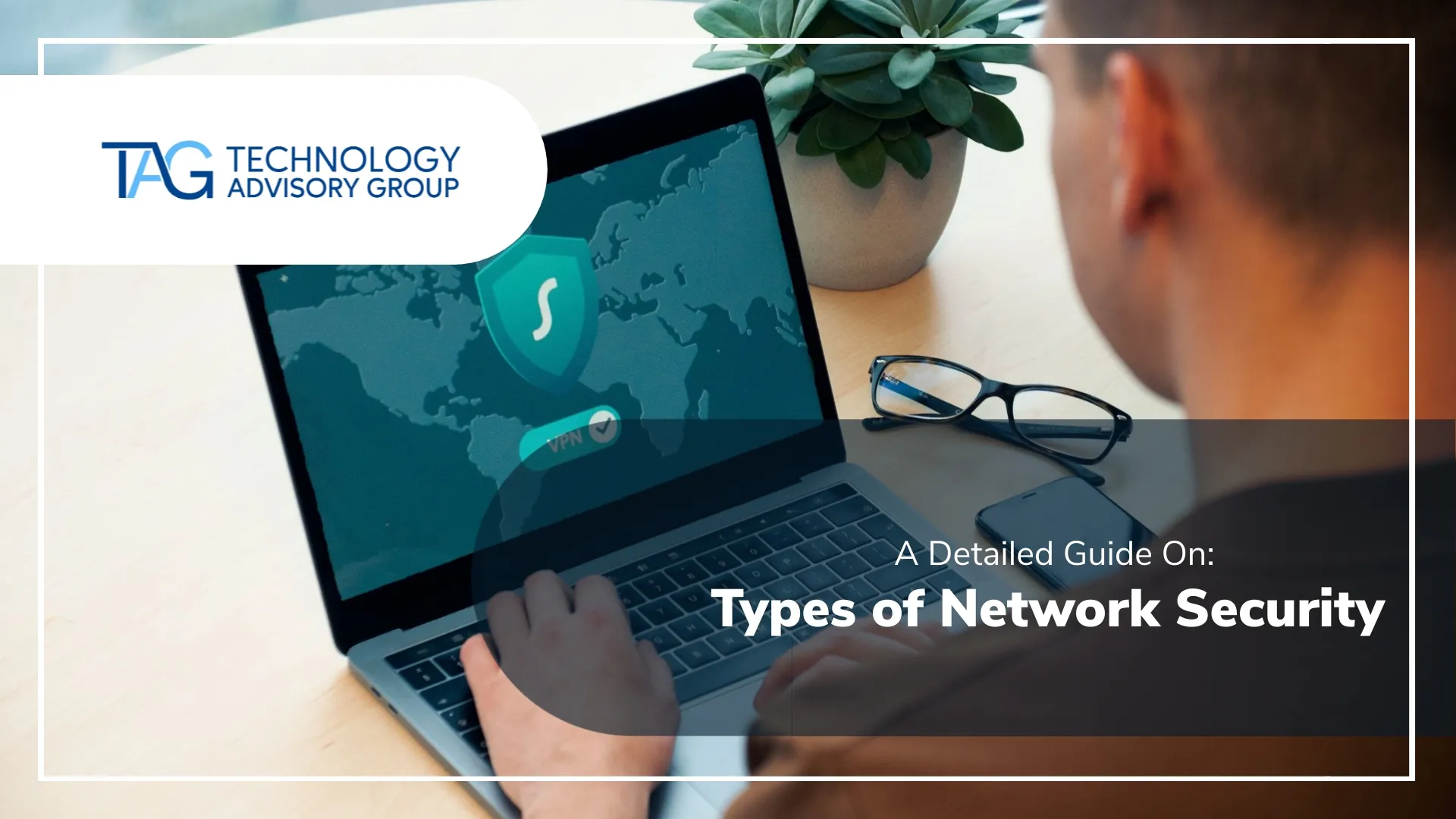
What is Network Security? Meaning, Types & Best Practices
Think of your business's network like a vault holding your most valuable secrets. Now, imagine that the vault has multiple hidden doors, each being targeted by skilled thieves every minute of every day. This is the reality of network security today. It's a constant...
Small Business IT Support Pricing Explained
Every entrepreneur feels the pinch of unforeseen expenses, especially when it comes to IT-related disruptions. But what if there was a strategy to minimize or even sidestep these costs? A study by Orange Matter revealed that the average cost of an unexpected IT...
9 IT Help Desk Best Practices You Need to Know
Having IT troubles? You’re not the only one. Both small and big businesses face IT challenges, which can mess up their day, lead to unhappy customers, and waste time and money. Think about this: small businesses can lose between $137 to $427 every minute when...
How to Create a Business IT Strategy
Creating an effective business IT strategy is essential for business success. With easy access to powerful software and online services, having the right IT infrastructure can be the difference between taking your business to new heights or keeping it stuck in a rut....
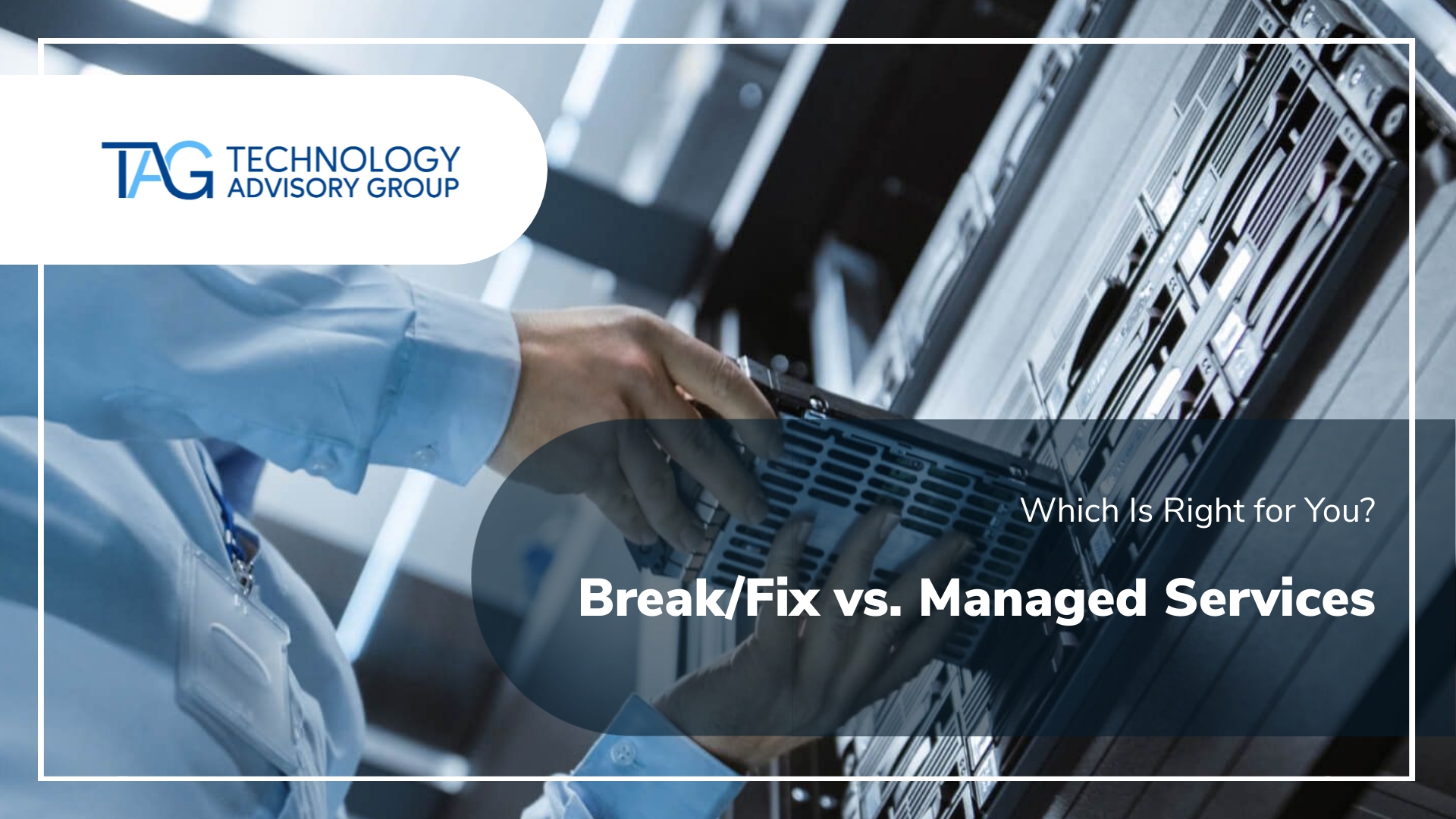
Everything You Need to Know: Break/Fix vs. Managed Services
In today’s fast-paced digital world, businesses can’t afford to have their IT systems down even for a moment. Did you know that downtime can cost small businesses up to $5,600 per hour? As the digital landscape evolves, so does the complexity of IT challenges. “In the...
What is Cloud Computing Security?
As a small to medium-sized business owner, you know that managing your IT infrastructure can be a daunting task.
The Best Methods for Mitigating Cloud Migration Challenges
More than 90% of organizations use the cloud for various applications as it has become one of the most in-demand services due to its dynamic technology and online collaboration.
Understanding the Importance of Network Security
Businesses face considerable IT demands considering the IT infrastructure, systems, applications, and cloud services needed to power their operations. Managing these challenges internally is not always possible and also may not be the best option.
The Differences Between IT Support vs.Help Desk
Businesses face considerable IT demands considering the IT infrastructure, systems, applications, and cloud services needed to power their operations. Managing these challenges internally is not always possible and also may not be the best option.
7 Benefits of Outsourcing IT Services You Should Know About
Businesses face considerable IT demands considering the IT infrastructure, systems, applications, and cloud services needed to power their operations. Managing these challenges internally is not always possible and also may not be the best option.
Managed Services vs. Professional Services
The comparison of managed services vs. professional services can be understood by examining the major differences between the two. First, managed IT services refer to outsourcing specific technology management tasks, such as network monitoring and security or...
The 6 Biggest Benefits of Managed IT Services
Finding an IT solution to fit your unique business can seem overwhelming. Legacy systems are in constant need of updating, and it can be confusing and time-consuming to migrate all your data to the cloud. From 2020-2021, cyber attacks increased by 15% and continue to...
Cyber Insurance Costs: What You Need to Know
In 2022, the average cost of a data breach for businesses reached roughly $4.35 million. With startling statistics like that, it's no wonder that many businesses are beefing up their cyber security measures (many of whom opt to benefit from the expertise of a...
Cloud Migration Project Plan Checklist
A complete or partial cloud migration is essential to your organization’s digital transformation. The sophistication of cloud computing, combined with an increasingly distributed workforce, means that more and more businesses are making the move. When implemented...
7 Elements and Components of a Business Continuity Plan
Data breaches, natural disasters, and other business disruptions can significantly impact your business, but they don’t have to. By understanding and applying the key elements of a business continuity plan (BCP), you can reduce the threat of disasters by guaranteeing...
















![What to Look For in Managed IT Services [Checklist]](https://www.techadvisory.com/wp-content/uploads/2025/02/Managed-IT-Services-Checklist-1.webp)