Cloud computing has emerged on the scene as a game-changer in recent years, offering the benefits of unparalleled convenience, scalability, and cost-efficiency to your technology endeavors.
However, as you increasingly rely on cloud services, it is essential to understand the importance of cloud computing security as well as the different cloud security challenges in order to stay ahead of potential threats.
In this guide, we will explore the question of “what is cloud security?”, discussing various threats that can compromise your data and providing practical security measures to mitigate those risks.
What is Cloud Computing Security? Understanding the Role
What is cloud security? Cloud computing security refers to the set of policies, technologies, and practices designed for protecting data, applications, and infrastructure in cloud computing environments.
It aims to ensure the confidentiality, integrity, and availability of data stored and processed in the cloud. By employing robust security measures, cloud providers and users can minimize the risk of unauthorized access, data breaches, and other security incidents.
1. What is infrastructure security in cloud computing?
Infrastructure security in cloud computing refers to the security measures put in place to protect the underlying physical and virtual resources that support cloud services. This includes servers, storage devices, networks, and networking equipment.
2. What is workload security in cloud computing?
Cloud workload security is a concept focused on protecting the integrity of workloads, which are sets of computing tasks, running in cloud environments.
3. What is data security in cloud computing?
Data security in cloud computing involves a range of measures designed to protect data stored in the cloud from loss, leakage, and theft. This includes encryption, which renders data unreadable without a cryptographic key, as well as access controls, which ensure only authorized users can access certain data.
While cloud security may seem complex, all of these areas boil down to one underlying purpose: protecting your data and systems.
Let’s take a look at what cloud security threats you are on the lookout for and how to stay protected.
Is Your Cloud Environment Secure?Get your complimentary vulnerability assessment NOW! |
Cloud Security Threats to Look Out For
Although still the more secure option in comparison to traditional data centers, 45% of all security breaches occur in the cloud. This is particularly caused by having a lack of proper cloud security solutions and employee training in place – which proves especially true as according to Gartner, 99% of all cloud security failures are due to human error.
What cloud security threats are important to be aware of as a business?
- Data breaches
- Malware and viruses
- Insider threats
- Data loss
- Denial of service (DDoS)
- Insecure application programming (APIs)
The need for optimal cloud security has become so prevalent that the cloud security market will reach USD 77.5 billion by 2026.
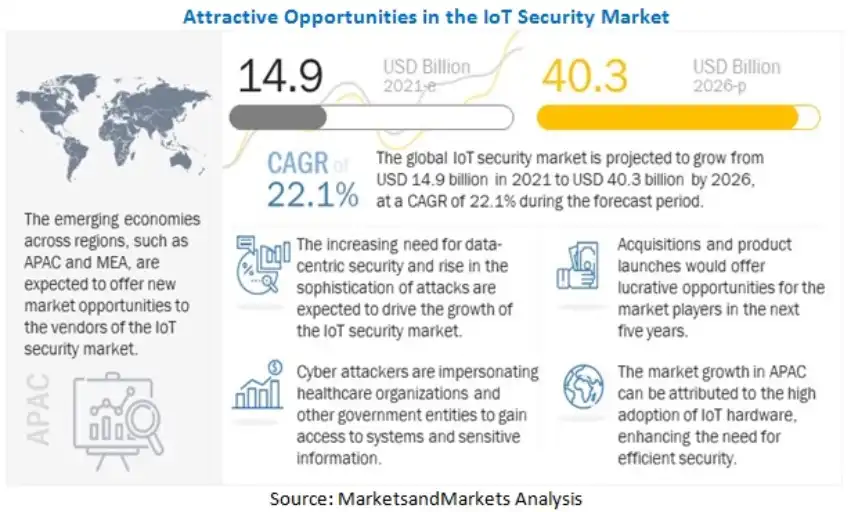
Image Credit: Markets and Markets
How to Mitigate Cloud Security Threats: Tips & Best Practices
Now that we understand why cloud security is important and have answered the general question of “what is cloud computing security?”, let’s consider the network security best practices to protect your data in the cloud.
1. Choose a reputable cloud service provider:
Selecting a reputable and reliable cloud service provider is essential. Consider their security certifications, data encryption practices, incident response capabilities, and commitment to data privacy.
2. Implement strong access controls:
Ensure that proper access controls are in place, including strong passwords, multi-factor authentication, and role-based permissions. Regularly review and update user access privileges to minimize the risk of unauthorized access.
3. Encrypt sensitive data:
Implement end-to-end encryption to protect sensitive data both in transit and at rest. Encryption ensures that even if unauthorized access occurs, the data remains unreadable and unusable.
4. Regularly update and patch systems:
Keep cloud systems and applications up to date with the latest security controls and patches. Regularly apply updates and patches provided by the cloud service provider to address vulnerabilities and protect against emerging threats.
5. Conduct employee training and awareness programs:
Educate employees about cloud computing services and security responsibilities for their role in maintaining data security. Regular training programs can help prevent social engineering attacks and reinforce good security habits.
| Check out these additional resources to learn more on how to stay secure during your cloud migration: |
How a Managed Service Provider Can Help You Mitigate Cloud Security Threats
Your cloud service provider, AKA your managed service provider (MSP), plays a crucial role in mitigating cloud security threats by implementing robust security measures and offering specialized services.
These typically fall into three broad categories including:
- Infrastructure as a service (IaaS)
- Software as a service (SaaS)
- Platform as a service (PaaS)
For over two decades, Technology Advisory Group (TAG) has been helping organizations like yours perfect their internal cloud security landscapes – and we want to help you too! Contact us now.to learn more about how we can help you mitigate cloud security threats for a secure tomorrow.
Schedule Your Cloud Services Consultation
Ready to make a move to the cloud? TAG is ready to help with any or all cloud services from a private cloud, public cloud, or Microsoft 365 services.
