Cybercriminals are always finding new ways to exploit weaknesses in your network, and it only takes one successful attack to cause serious damage to your business.
And with the increasing complexity of technology, it can be especially challenging to keep up with the latest cyber threats and vulnerabilities.
In this blog, we will explore some of the most common network vulnerabilities – and more importantly – how a managed service provider (MSP) can help keep you protected from all the different types of attacks in network security!
Understanding the Severity of Network Vulnerabilities
With new types of cyber vulnerabilities on the rise everyday, the cost of cybercrime is predicted to hit $8 trillion in 2023.
And in the event that your cyber vulnerabilities are exploited, this can result in significant financial losses, reputational damage, and legal implications.
Making the investment in a proper cyber security plan is essential to the long-term success of your business. Especially considering that over 60% of SMBs go out of business after their first cyber attack.
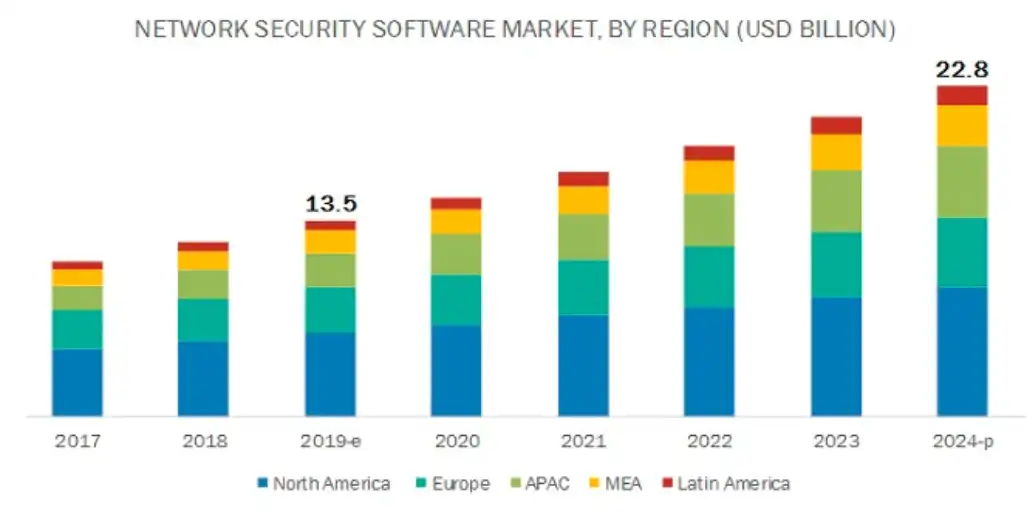
Image Credit: Markets and Markets
Let’s take a look at some of the most common types of cyber security vulnerabilities and how you can ensure the safety of your sensitive data and systems with the help of an MSP.
4 Common Types of Attacks in Network Security
Malware: Malware is a type of software designed to damage, disrupt, or gain unauthorized access to a computer system.
These types of attacks in network security can be devastating to your business, as they can result in data theft, financial losses, and system crashes. Malware can come in many forms, including viruses, trojans, ransomware, and spyware.
Phishing Attacks: Phishing attacks are a type of social engineering attack that tricks users into divulging sensitive information such as login credentials, credit card numbers, or other personal information.
Among the most common network vulnerabilities, phishing attacks often come in the form of an email that appears to be from a trusted source. Once the user clicks on the link in the email, they are taken to a fake website that looks legitimate, where they are prompted to enter their sensitive information.
Phishing attacks increased by 48% in the first six months of 2022, with reports of up to 11,395 incidents costing organizations a total of $12.3 million for these cyber security vulnerabilities alone.
Ransomware: Ransomware is a type of malware that encrypts a victim’s files and demands payment in exchange for the decryption key.
As another one of the most common types of network security threats, ransomware attacks can be devastating to businesses, resulting in the loss of critical data, financial losses, and reputational damage.
Insider Threats: Insider threats refer to malicious or unintentional actions taken by employees, contractors, or other trusted individuals who have access to your network. Insider threats can include stealing sensitive information, installing malware, or accidentally causing data breaches.
Check out these additional resources to learn about how an MSP can keep your data protected from the ever-evolving landscape of cyber threats and vulnerabilities: |
Why Are These Threats Successful?
Cybercriminals are successful in their attacks because they exploit your network security vulnerabilities – aka, weaknesses in your cybersecurity strategy.
These types of vulnerabilities in network security are more common than you think and typically include:
- Unpatched software
- Misconfigured firewalls
- Outdated software
- Weak passwords
- Unsecured wireless computer networks
- Untrained employees
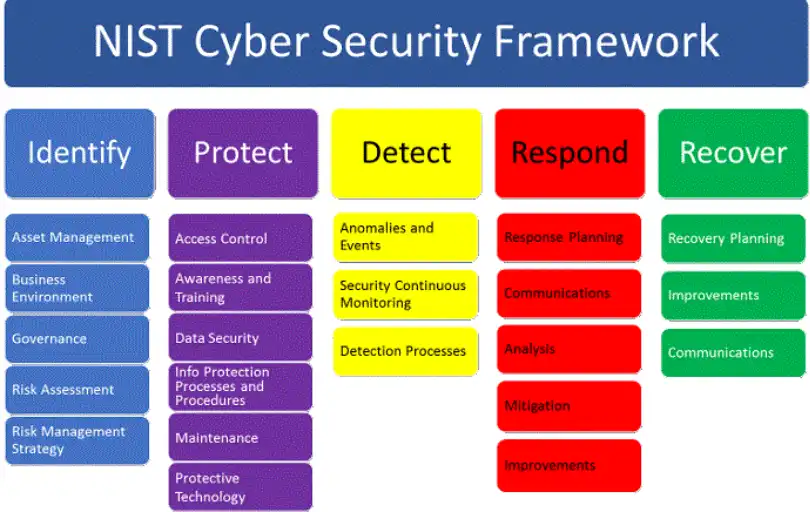
Image Credit: Dark Reading
An MSP can help keep you protected from these types of network security threats by implementing a comprehensive security strategy tailored to your business’s unique needs.
Let’s take a closer look at what exactly that entails.
How Can an MSP Help Keep You Protected?
1. Proactive Monitoring and Maintenance
MSPs can monitor your network 24/7, identify potential security threats, and proactively address them before they become bigger problems.
Regular maintenance, including software updates and security patches, can help prevent network vulnerabilities from being exploited.
2. Employee Training and Awareness
An MSP can provide employee training and awareness programs to help your staff understand the importance of network security and identify potential security threats.
Regular training can help ensure that your employees are up-to-date with the latest security best practices and can help prevent social engineering and phishing attacks – this is your first line of defense since 88% of security breaches are a result of human error.
3. Data Backup and Disaster Recovery
Information security vulnerabilities are nothing to play around with.
Luckily, an MSP can help you develop a data backup and disaster recovery plan that ensures your critical data is safe and recoverable in the event of a cyberattack or other disaster.
Regular data backups can help prevent data loss, and a disaster recovery plan can help minimize downtime and ensure business continuity.
4. Network Security Audits
An MSP can perform regular network security audits and penetration tests to identify potential access points and network security vulnerabilities – and recommend solutions to address them.
Regular audits can help ensure that your operating systems are secure and compliant with industry standards and regulations.
Find Out What Information Security Vulnerabilities Are Putting Your Sensitive Data at Risk!Get a complimentary Security Risk Assessment today |
Mitigate Your Cyber Threats and Vulnerabilities With Our Support
Navigating the landscape of cyber threats and vulnerabilities can be daunting on your own, but with the help of an MSP as well as the right tools and resources – protecting your sensitive data and systems is easier than you think.
With over 25 years in business, Technology Advisory Group (TAG) is prepared to help you mitigate all the different types of vulnerabilities in network security.
Expose and reduce the risk of hackers from stealing data and gaining access to your network. Schedule your cybersecurity evaluation today!
Schedule Your Cloud Services Consultation
Ready to make a move to the cloud? TAG is ready to help with any or all cloud services from a private cloud, public cloud, or Microsoft 365 services.
