The line between safety and exposure is just one missed security update away. According to IBM’s 2024 Cost of a Data Breach Report, the average data breach now costs organizations a staggering $4.88 million—a sharp reminder that cybersecurity is no longer just an IT problem, but a boardroom priority.
Yet, despite the rising stakes, many businesses still approach cybersecurity with a patchwork of tools, vague policies, and wishful thinking.
| “A strong cybersecurity posture isn’t built overnight—it’s built with clarity, consistency, and a checklist that doesn’t miss the small stuff,” – Jason Harlam, Business Development Manager, Technology Advisory Group |
In this blog, we’re handing you The Ultimate Cybersecurity Assessment Checklist—your strategic blueprint for hardening your defenses, identifying weak links, and transforming guesswork into airtight assurance. Let’s lock it down.
Get 24/7 Protection From a Team With 25+ Years of Experience |
The Cybersecurity Fortification Framework: 8 Essential Zones of Defense
Before attackers exploit a vulnerability, they scout for weaknesses—misconfigured firewalls, unsecured endpoints, forgotten access privileges. One open door is all it takes. That’s why cybersecurity isn’t a single lock. It’s a fortress—built layer by layer, from your network perimeter to your compliance paperwork.
Below, we break down the 8 Essential Zones of Defense—the strategic pillars of your cybersecurity assessment.
1. Network Security – Fortify the Front Door
Think of your network as the outer wall of your castle. It’s the first point of contact between your infrastructure and the unpredictable world of the internet. If there are cracks in that wall, attackers will find them.
Why It Matters:
Unsecured networks are prime targets for DDoS attacks, man-in-the-middle interceptions, and lateral movement within your systems once a threat actor gets in.
To-do Checklist:
- Firewall Configuration Audit – Check for overly permissive rules, unlogged exceptions, and legacy configurations.
- Close Unused Ports and Services – Attackers often scan for these to find a way in.
- Segment Your Network – Separate guest access, IoT devices, and sensitive internal systems.
- Enable Intrusion Detection & Prevention (IDPS) – Flag anomalies and stop attacks in real-time.
- Use VPNs for Remote Access – Encrypt connections and authenticate users securely.
Bonus Tip: Employ zero-trust architecture to ensure every connection is verified, no matter where it originates.
2. Endpoint Protection – Secure Every Device
Every device is a doorway. Every click is a potential entry point. Laptops, mobile phones, and smart printers are all attack surfaces if not locked down.
Why It Matters:
A single compromised device can become a launchpad for malware distribution, data theft, or full-on network infiltration.
To-do Checklist:
- Install Anti-Malware & Antivirus – Make sure it auto-updates and scans regularly.
- Enable Full-Disk Encryption – Protect data even if a device is stolen or lost.
- Disable USB Access or Use Endpoint Control – USB drives are notorious malware carriers.
- Automate OS & App Updates – Ensure vulnerabilities are patched without delay.
- Deploy Mobile Device Management (MDM) – Enforce security settings remotely.
3. User Access Controls – Limit the Blast Radius
Humans are helpful, but over-permissioned users can accidentally (or maliciously) cause catastrophic damage. Access controls reduce the risk.
Why It Matters:
When everyone has admin privileges, attackers only need to phish one user to gain full control.
To-do Checklist:
- Role-Based Access Control (RBAC) – Give users access only to the data they need.
- Strong Password Policies – Enforce complexity, length, and password rotation.
- Deploy Multi-Factor Authentication (MFA) – Passwords alone are not enough.
- Quarterly Access Reviews – Revoke unnecessary privileges before they become dangerous.
- Immediate Deprovisioning of Ex-Employees – Automate this process for zero lag.
Consider Just-In-Time access provisioning for highly sensitive resources.
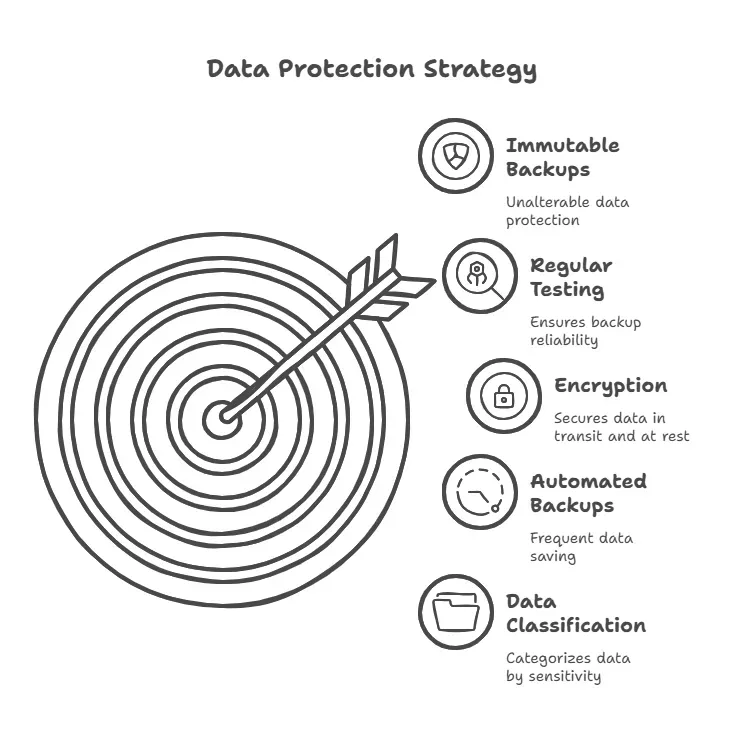
4. Data Protection & Backup
Your data is more than files—it’s your company’s memory, reputation, and value proposition rolled into one. When it’s lost or compromised, you’re not just recovering information—you’re fighting to restore confidence.
Why It Matters:
Ransomware actors specifically target backup files, knowing they’re your only lifeline.
To-do Checklist:
- Classify Data by Sensitivity – Apply the right level of protection to each category.
- Encrypt Data In Transit & At Rest – Use strong encryption protocols like AES-256.
- Automated Backups – Schedule frequent, automatic backups to off-site or cloud locations.
- Test Restores Regularly – Don’t assume your backups work—prove it.
- Use Immutable Backups – These can’t be altered or deleted, even by ransomware.
Stat Check: According to Sophos, 94% of organizations hit by ransomware in 2023 said attackers tried to compromise their backups.
5. Patch Management – Plug the Holes Before They’re Exploited
Hackers don’t need to invent new threats when businesses leave the door open with unpatched vulnerabilities. Staying updated isn’t just maintenance, it’s a frontline defense.
Why It Matters:
Delaying patches turns known vulnerabilities into open invitations, giving attackers months of opportunity to exploit what could’ve been fixed in minutes.
To-do Checklist:
- Real-Time Asset Inventory – Know what hardware/software is in use at all times.
- Monitor CVE Databases & Vendor Alerts – Stay on top of vulnerability disclosures.
- Prioritize by Risk – Patch the most critical vulnerabilities first.
- Automate Where Possible – Let tools handle low-risk patching across systems.
- Maintain a Patch Log – For audit trails and incident response context.
Field Insight: Patch management should be tied to change control policies to avoid surprises during updates.
| Read More About How You Can Protect Your IT Systems |
6. Security Awareness Training – Human Firewalls Matter
The best security systems can’t stop an employee who unknowingly clicks a malicious link. Your team needs to be as alert as your tech.
Why It Matters:
Humans are statistically the most likely breach vector, whether through phishing, poor password hygiene, or accidental data sharing.
To-do Checklist:
- Annual Cybersecurity Training – Cover phishing, social engineering, and secure behavior.
- Phishing Simulations – Run monthly or quarterly tests and track results.
- Visual Reminders – Posters, wallpapers, and login splash screens can reinforce secure habits.
- Open Reporting Culture – No fear in flagging potential threats or mistakes.
- Gamify Training – Offer incentives for high participation or catching real threats.
Stat to Remember: 80% of organizations report that security awareness training has significantly reduced phishing susceptibility.
7. Incident Response Planning – Train for the Worst Day
Cybersecurity isn’t about if an incident will happen—it’s about how well you respond when it does. Speed and structure make the difference.
Why It Matters:
Without a tested plan, incidents turn into chaos. Delays cost time, money, and reputation.
To-do Checklist:
- Develop a Formal IR Plan – Include detection, containment, eradication, recovery, and lessons learned.
- Define Roles & Response Teams – Who calls the shots during an emergency?
- Keep Contact Info Current – Vendors, regulators, legal counsel, media contacts.
- Run Tabletop Exercises – Simulate attacks and rehearse response steps.
- Partner with an MSSP or IR Firm – For added muscle during major breaches.
Bonus Tip: Store a hard copy of your IR plan offline—attackers love encrypting the digital version.
8. Compliance & Auditing – Be Secure and Show It
Security without documentation is invisible. Regulators, clients, and auditors want to see that you’re secure.
Why It Matters:
Whether you’re in healthcare, finance, or tech, proving compliance is non-negotiable—and getting stricter every year.
To-do Checklist:
- Map Out Applicable Regulations – HIPAA, PCI-DSS, CCPA, SOC 2, etc.
- Keep Detailed Audit Trails – Every policy change, login, and access attempt matters.
- Conduct Annual Security Audits – Internal or external.
- Document Retention Policies – Know how long you store sensitive info and why.
- Assign a Compliance Lead – Or outsource to a consultant with industry knowledge.
Insight: Use GRC (Governance, Risk, and Compliance) tools to streamline documentation, controls, and audit readiness.
Strategic Cybersecurity Assessment Summary Table
| Checkpoint | What’s the Goal? | Key Questions to Ask | Suggested Tools/Frameworks |
| 1. Inventory Assets | Know exactly what needs protection | What devices, software, and data are in use? Who has access? | Smartsheet Templates, IT Glue |
| 2. Scan for Vulnerabilities | Find the weakest spots before attackers do | Are systems patched? Are configurations secure? Are passwords strong? | FortifyData, Nessus Scanner |
| 3. Identify Threats | Understand what you’re up against | What are the most likely threats (phishing, ransomware, insider abuse)? | SentinelOne 101, CISA Alerts |
| 4. Analyze Risk Impact | Prioritize what matters most | What would a breach cost us? What can we not afford to lose? | NIST Framework, FAIR Risk Model |
| 5. Implement Safeguards | Block, detect, and respond to attacks | Do we have MFA, firewalls, EDR, encryption in place? | Microsoft Defender, Cisco Umbrella |
| 6. Train Your People | Turn employees into your first line of defense | Do staff recognize phishing? Do they follow best practices? | KnowBe4, Infosec IQ |
| 7. Monitor & Improve Continuously | Stay ahead of evolving threats | Are we logging incidents? Are reviews happening regularly? | CrowdStrike, Splunk, SOC-as-a-Service |
Fortify Your Defenses with Technology Advisory Group (TAG)
Cybersecurity doesn’t have to be overwhelming, especially when you have the right partner in your corner.
At Technology Advisory Group (TAG), we help small and mid-sized businesses take control of their cybersecurity with:
- Comprehensive assessments
- Custom security strategies
- Ongoing monitoring and user training
Whether you’re starting from scratch or fine-tuning your defenses, TAG has the expertise to secure what matters most. Contact TAG today to schedule your tailored cybersecurity assessment and protect your business from today’s threats and tomorrow’s unknowns.
| Reduce Risks With New England’s Leading Cybersecurity Experts | |
| Providence, RI | Worcester, MA |
Schedule Your Cloud Services Consultation
Ready to make a move to the cloud? TAG is ready to help with any or all cloud services from a private cloud, public cloud, or Microsoft 365 services.


