In many ways, using a cloud infrastructure is more secure than hosting your data on-premise. 94% of businesses notice improved security after moving to the cloud, and 91% say it helps them meet their compliance requirements more easily. However, cloud malware is still a real concern.
| “It’s easy to assume that data stored in the cloud will be fully protected by the cloud provider at all times. The truth is that you still need to do your due diligence to remain secure.” – Jason Harlam, Business Development Manager, Technology Advisory Group |
The good news is that using the right security measures is all you need to do to reduce your risk of cloud attacks. These measures may not be quite the same as the measures you used to protect your on-premise data, but many of the general best practices will remain the same.
The rest of this article will explore that. We will go over the unique malware threats that you may face in the cloud and what you can do to reduce your risk of facing them.
8 Common Types of Malware Attacks in Cloud Computing
1. Hyberjacking
Hyperjacking is an attack that targets the part of the cloud system that manages all virtual machines. When attackers take control of this layer, they can secretly monitor or manipulate any virtual machine running on it. Since most security tools don’t look this deep, the malware can stay hidden while it collects data or disrupts operations.
2. Worm Propagation
This threat involves malware that spreads quickly from one cloud-based system to another within the same environment. It looks for weak points in how cloud systems are connected internally. Because it spreads without using the public internet, the infection can go unnoticed. This allows the attacker to reach many systems before any alerts are triggered.
Get 24/7 Protection From a Team With 25+ Years of Experience |
3. VM Injection
Attackers can create virtual machines that appear normal but contain hidden malware. They deploy these machines into a cloud environment using stolen login credentials or open access points. Once inside, the malware scans for sensitive data, collects passwords, or connects to outside systems controlled by the attacker.
4. Container Escape
Many companies use containers to run small parts of applications in the cloud. This type of malware starts inside one of those containers, then breaks out to gain unauthorized access to the larger system it runs on. Once out, it can access other containers, change settings, or spread further.
5. API Abuse
Cloud systems use APIs (application programming interfaces) to let different parts of the system talk to each other. Attackers use malware to take advantage of weak or unprotected APIs. Once in, they can change settings, steal data, or spin up new systems under their control. Because APIs are trusted tools, this kind of attack can be hard to spot.
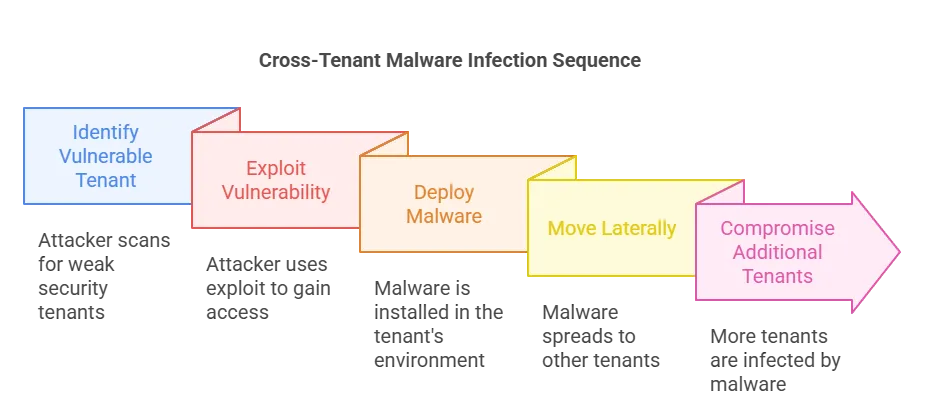
6. Cross-Tenant Attacks
Public cloud providers host multiple customers on shared systems. Malware used in cross-tenant attacks finds flaws that allow it to move from one customer’s environment into another. This breaks the separation that cloud services are supposed to enforce. Attackers can cross clouds and put sensitive data at risk even when one customer has no direct contact with the other.
7. Cloud Backdoors
A backdoor is hidden access that allows attackers to return to a system even after it has been cleaned or restarted. In cloud environments, this type of malware often hides in startup settings or automated tasks. It allows attackers to come back later without being noticed. These backdoors can stay active through system updates and even infrastructure changes.
8. Function-as-a-Service (FaaS) Malware
FaaS platforms run small pieces of code on demand, often used for automating tasks in the cloud. Attackers insert malware into these functions by using weak spots in how the code runs or by uploading harmful files. When the function activates, the malware runs briefly and disappears. This makes it difficult to detect and easy to repeat.
| Read More About How You Can Protect Your IT Systems |
8 Best Practices You Should Follow to Prevent Malware in Cloud Computing
1. Use Strong Access Controls
Limit access to cloud systems by applying the principle of least privilege. Each user or system should have only the permissions it needs to perform its job. This reduces the chance that malware can spread or access sensitive areas if an account is compromised.
2. Enable Multi-Factor Authentication (MFA)
Require more than a password to log in by adding a second form of verification, like a code sent to a phone or an authentication app. MFA makes it much harder for attackers to access cloud accounts using stolen credentials. This stops many common entry points used by malware.
3. Keep All Cloud Resources Up to Date
Apply patches and updates to cloud applications, virtual machines, containers, and any third-party tools you use. Updates fix known weaknesses that malware can exploit. Delaying them gives attackers more time to take advantage of security flaws. In fact, 97% of tested applications contain at least one vulnerability.
For example, here is an overview of various cloud components and why updating them will decrease your attack surface.
| Cloud Component | Risks of Delaying Updates | How Updates Help Protect You |
| Virtual Machines | Hackers can break in using old system bugs | Fixes those bugs before hackers can use them |
| Containers | Bad code can get in through old versions | Replaces risky versions with safer ones |
| Web Apps | Attackers can steal data or control the app | Blocks known ways attackers break in |
| Third-Party Tools | Hackers can use weak spots to get into your system | Closes those weak spots so they can’t get in |
| Cloud Dashboards (portals) | Hackers can take over accounts or settings | Fixes problems in the dashboard before they’re used against you |
4. Monitor API Activity Closely
Watch for unusual or unauthorized use of cloud APIs, which are often used to manage services and access data. Malware often targets APIs because they offer direct control over cloud resources. Regular monitoring helps you spot suspicious behavior before it causes harm.
5. Use Endpoint Protection for Cloud Workloads
Install security software on cloud-based virtual machines and containers, not just on employee devices. These tools detect and block malware before it can spread or perform malicious actions. Cloud workloads need the same protection as on-premises systems.
6. Limit Use of Public IP Addresses
Only expose systems to the internet when absolutely necessary, and use private IP ranges for internal communication. Malware often enters through public-facing services with weak or missing protections. Reducing exposure lowers the number of possible entry points.
Public-facing IP addresses are also more likely to fall within high-risk networks—less than 2% of IP address space receives over 5% of total internet traffic, much of it linked to malicious activity.
7. Use Logging & Alerting Tools
Turn on detailed logging for cloud activities and set alerts for abnormal patterns. This allows your team to investigate and respond quickly if something looks suspicious. The faster you detect an issue, the easier it is to contain.
8. Perform Regular Security Audits
Check your cloud configurations and access settings on a regular schedule. These audits help you find mistakes, unnecessary permissions, or outdated components that malware could exploit. Fixing issues early reduces the overall risk to your environment.
| Reduce Risks With New England’s Leading Cybersecurity Experts | |
| Providence, RI | Worcester, MA |
Work With a Team of Cybersecurity Experts to Lower Your Risks
Implementing these best practices can significantly reduce the risk of cloud-based malware attacks. However, navigating the complexities of cloud security requires expertise and constant vigilance. Partnering with a trusted IT service provider can ensure your business remains protected against evolving cyber threats.
Technology Advisory Group (TAG) offers comprehensive cybersecurity solutions tailored to protect your cloud infrastructure. Our service includes managed SOC, endpoint security, and cloud-focused cybersecurity. Plus, our proactive approach includes regular security audits, real-time monitoring, and rapid response to potential threats.
Reach out to us today to secure your cloud storage.
Schedule Your Cloud Services Consultation
Ready to make a move to the cloud? TAG is ready to help with any or all cloud services from a private cloud, public cloud, or Microsoft 365 services.


